By definition, phishing is the practice of manipulating individuals into divulging personal information, often by posing as a trustworthy persona online.
Hackers and other types of cybercriminals use this cyber attack technique to obtain sensitive information such as usernames, passwords, credit card numbers, and more.
Phishing is one of many forms of cyber attacks that pose enormous risks to companies of every size.
In fact, a successful phishing attack can lead to data breaches that have been reported to cost an average of $4.45 million, according to a 2023 study from IBM.
There are many ways to prevent this type of cyber attack, but it all starts with understanding how phishing works and the sneaky tactics hackers use to put you at risk.
Keep reading to learn the ins and outs of phishing and how to avoid putting your sensitive personal and financial data at risk.

What phishing?
In a phishing attack or phishing scam, a malicious person, usually called a hacker or cybercriminal, seeks the contact information of random users.
They sometimes target a particular company or organization but often cast a wide net online to catch as many people as possible — hence the term "phishing."
Phishing scams trick users into giving their most sensitive information, often through the use of manipulative psychological tactics.
For example, they may take on an authoritative or trustworthy persona, such as a customer service representative or government collection agent, convincing individuals to give their information.
An attacker may also leave a message with language that produces a strong sense of urgency, eliciting an emotion of panic that can often trick users into giving up sensitive info in order to fix a completely made-up scenario.
Those are just a few general ways hackers can perform phishing. There are numerous types of phishing techniques cybercriminals will use to steal vital information from individuals and businesses alike.

The different types of phishing attacks
Today, communication occurs over various devices and channels, making others easier than ever to reach — even for hackers.
Each new mode of contact offers opportunities for phishing scammers to obtain private info.
However, the different types of phishing that are out there don't just differ in the method of reaching an individual but also who the attacker is targeting.
Here is a list of several critical phishing attempts to watch out for:
Email phishing attacks
The most prevalent phishing scams out there are often phishing emails — better known as spam messages.
It is easy to spot a phishing email as they all share a few of the same elements that will appear suspicious to a trained eye. Here are some to consider:
- A phishing email is often sent from a public email domain, i.e. "@gmail.com," "@outlook.com," or another public email domain.
- The main content of phishing emails is often poorly written, with several misspelled words and clearly bad grammar.
- Many phishing emails will prompt users to click on an unfamiliar or suspicious link. This often ends up being a malicious link that may send a user to a phishing website or cause them to download malware onto their device unintentionally.
- The message may also appear similar to official emails from trusted businesses and providers, but upon closer inspection, it looks "off" and uses different fonts, colors, and text sizes than normal.
These are all basic but effective signs to look out for whenever one finds suspicious emails in their inbox.
Fortunately, electronic messaging systems like Gmail have become progressively better at creating spam filters so users can browse their personal emails more easily without fear of a phishing attack.
SMS phishing attacks
Similar to email phishing, SMS phishing involves an attacker reaching targeted users through their mobile devices via text message rather than email.
Also known as "smishing," phishing messages appear very similar to phishing emails but may differ in length and alleged sources.
For example, a phishing email will contain several paragraphs of content with the attacker posing as a representative from the receiver's cable company.
On the other hand, a phishing text message will be shorter and may come from more casual personas, such as a friend or acquaintance from the user's workplace.
However, both types of phishing attacks have the same goals: utilizing urgent language to create a sense of immediacy and panic, unfamiliar links to fraudulent web pages, or sudden requests for highly sensitive personal information for made-up reasons.
Voice phishing attacks
In addition to email and text messages, voice phishing — also known as "vishing" — involves the attacker attempting to deceive individuals into providing sensitive information through one or more phone calls.
This method most often involves impersonating legitimate entities, such as government agencies, businesses, banks, or other financial institutions.
As with any type of phishing, the attacker will make false claims using urgent or threatening language to convince the receiver to divulge vital personal information, such as their credit card number, routing and bank account numbers, and more.
These calls are often unsolicited but can appear official based on the caller ID, which the attacker can often fake or "spoof" to appear more legitimate.
Spear phishing attacks
This type of phishing attack can involve one or more of the previous phishing types but strongly differs in who the attacker is targeting.
Common phishing attacks are focused on the general public, while a spear phishing attack will concentrate on a particular individual or organization.
This type of phishing involves the attacker taking more time to gather information about the target individual or company.
Their attempts are often more thorough and compelling, as they utilize personalized information that they've gathered to appear familiar and connected to their target.
Spear phishing is a much more goal-oriented type of phishing, as the attacker sees value and purpose in obtaining sensitive information from the group or individuals they have set their sights on, usually because they are wealthy executives with extensive bank accounts or VIPs with high-level information in their systems.
Whatever the reason, governments, agencies, and businesses need to protect themselves and their information from this highly refined form of phishing.
"Whaling" attacks
Simply put, "whaling" is a form of spear phishing that directly targets high-value individuals with access to valuable data or systems and credentials to highly lucrative business accounts that an attacker may seek to steal.
Top executives of giant corporations are often the target of these phishing attempts, as their credentials give them access to incredible amounts of information and financial resources, all of which can be used for enormous profits if a crafty individual were to steal them.
The sheer amount of value these targets hold is why this form of spear phishing is further specified as "whaling."
Angler phishing attacks
Yet another highly specific type of phishing attack that has become more common is "angler phishing." This involves scam artists and hackers who use fake social media accounts to impersonate customer support representatives.
First, they observe the activities of official customer support accounts on platforms such as Twitter or Instagram. They then create a fake account with a handle that appears legitimate enough to trick users into contacting them for questions and complaints.
The attacker will then ask for the users' personally identifiable information or redirect them through a malicious link to a fake website that will install malware without the users' knowledge.
Finally, the angler phishing attacker will use the information they obtained to perform further scams for even more sensitive information or steal their victims' identities and financial resources.
Knowing all these different types of phishing campaigns can help individuals and businesses detect phishing attempts before they result in malicious attackers obtaining their most sensitive data and personal information.
Why hackers perform phishing attacks
Hackers have numerous motivations behind their phishing scams. Here are a few general reasons they may have in attempting to scam a business or individual from their most important private information:
Performing identity theft to steal money or information
Cybercriminals often perform phishing as a way to gain whatever information they can to steal an unsuspecting victim's identity. They can simply start with an email address and, through their phishing efforts, gather even more personal details that will eventually allow them to steal their target's identity.
Divulging sensitive data from individuals or businesses
After stealing their identity, hackers may intend to go even deeper by using their victim's credentials to access their employers' network to gather confidential information.
They may also pose as their victims through their email addresses, sending messages to friends, family, and colleagues to gather even more sensitive information.
Holding the network of a company or financial institution hostage
Phishing can also allow malicious actors to perform what is known as a ransomware attack. By utilizing precise spear phishing attacks, a dedicated hacker can access a business's network and install malware to take control of its shared memory storage.
The attacker can then contact the business and demand payment or threaten to delete all company data.
Because we rely on technology at nearly every level, a series of successful phishing attacks can eventually lead to devastating threats to the livelihoods of individuals and businesses alike.
Therefore, it is vital to stay aware of phishing scammers' methods and to protect one's personal information at all costs.
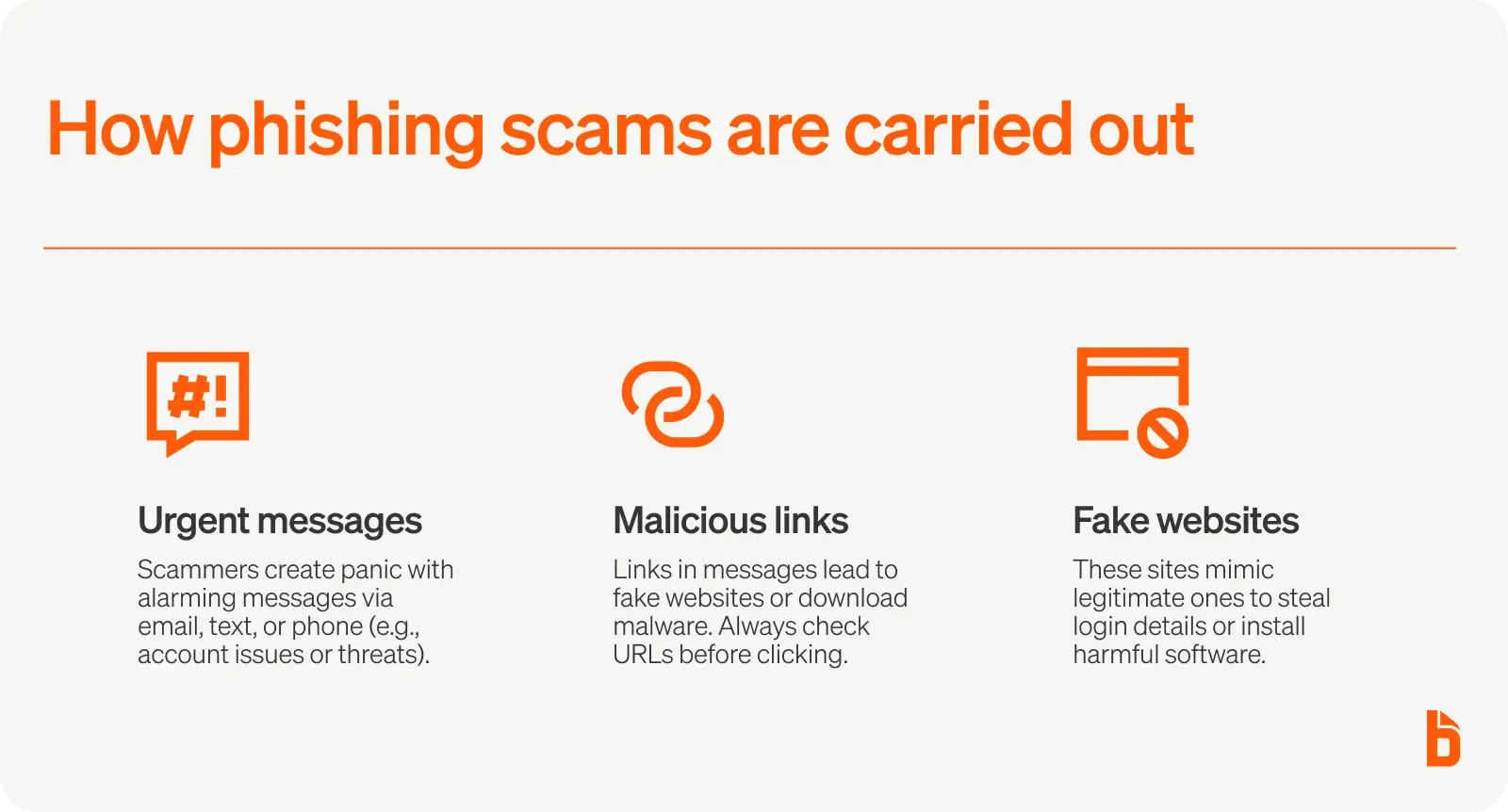
How are phishing scams carried out?
Phishing scams are performed in various ways, each sharing a few of the same elements we share below.
The most important thing is to stay aware and suspicious when a message, web link, or website appears less legit than it should. Here are a few key ways phishing scammers carry out their schemes:
Messages with a sense of urgency
Whether through emails, text messages, or phone calls, phishing scammers will primarily try to contact their target with an urgent message that can put individuals in a state of panic.
The message is often personal, such as, "Pay your fees now, or we will foreclose on your home!" or "There is an issue with your credit card; please click the link below to verify your identity."
Malicious links
Part of a scammer's message may also contain a malicious link that, if clicked, will redirect the user to a scammer's website or cause malware to download onto their computer.
A good idea is to hover the mouse cursor over the link to see the URL it leads to. Often, it will not be a secure or trustworthy site.
Fake websites
Another essential aspect of a scammer's attempts is fake websites, which they may leave links to in their phishing messages to users or they may also take over compromised websites with poor security features.
These will allow them to redirect users visiting the site to the scammer's fake website instead.
The website may automatically load malware to a user's system or convince them to provide their legitimate username and password for a more legitimate site, providing the scammer with further access.
Knowing these central elements of a phishing scam can help one avoid them, but it is also essential to develop proactive methods of preventing them and minimizing the risks they bring to themselves or their business.

How to prevent phishing attempts
To combat phishing, individuals and businesses should practice maintaining phishing awareness while utilizing their systems.
To ensure their internal data security, companies should hold routine user training seminars dedicated to teaching their employees about anti-phishing strategies and perform random phishing simulations to ensure their staff continually internalizes these strategies.
Here are some of them for both individuals and organizations to consider:
Avoid responding to unfamiliar emails & text messages
Unsolicited texts and emails from seemingly random people are best left ignored and deleted.
These are often phishing attempts in which scammers are seeking to confirm whether the number or email address they have stolen is held by a real person they can continue to target.
Never visit potential phishing websites
A strong signal indicates a website's trustworthiness if its URL begins with the letters "https," which stands for "Hypertext Transfer Protocol Secure."
In short, this is a more encrypted, secure version of HTTP, providing greater security for websites and users, and is also a standard among legitimate websites today.
If a website or link URL doesn't include an "https" at the beginning, then it is, at best, unsecured and, at worst, a malicious website and should be avoided.
Be careful with your personal or financial information
Individuals and businesses should be protective of their online accounts across the internet, including their social media.
Hackers will take whatever information is available to piece together a way to perform more detailed phishing scams. Keep all accounts private or devoid of personal or confidential information.
Also, be sure to only share such information with trusted parties and no one else while online.
Consistently report phishing attempts
Another strong strategy is to report any and all phishing attempts to authorities such as the Federal Trade Commission or the Anti-Phishing Working Group.
Reporting can help prevent further attempts from occurring and broaden information on the latest phishing methods as well.
In addition, businesses should immediately notify customers in danger of identity theft due to a recent breach resulting from a phishing attack.
Install anti-phishing software
All information systems should also contain anti-phishing software, especially businesses with large-scale data storage in their facilities or elsewhere.
For individuals, this may come in the form of commercial anti-virus software, which often includes features that help fight against phishing attempts.
Use secure, well-encrypted software systems
Finally, another way to prevent phishing scams is to stay diligent and try only to use software systems that contain strong encryptions and have a solid track record of security.
Though there are no guarantees when fighting against phishing scams, it helps to work with companies that seek to ensure the highest data and information security standards.
Keep your financial information safe
Phishing can become an enormous problem for businesses, especially if attackers are seeking to gain access to your company's financial system.
Follow the tips and best practices above and stay vigilant to keep your data safe and out of the hands of cyber-criminals.


